How to write a rescreening policy that holds up in an audit


What you will learn: how to design a proportionate, auditable rescreening policy that you can defend to reviewers, clients and employees.
Before you start: list your sensitive roles, the countries you operate in, and any client clauses that mention ongoing personnel checks. You will use these three inputs in every section below.
1) Purpose and scope
Teach the concept
Auditors begin with intent and coverage. Your policy must explain why rescreening exists, who it applies to, and where it applies. Keep it short and precise. Avoid vague phrases like “periodic checks” without a reason.
How to write it
- State the objective in one sentence.
- Name the populations covered, including contractors and agency staff.
- Mention that country addenda apply where local law differs.
- Reference the lawful basis at a high level. You will detail this in your global rollout notes.
Example you can adapt
Purpose. This policy sets a proportionate and repeatable approach to rescreening employees and contractors to manage insider risk, meet client expectations, and provide evidence for audits and renewals.
Scope. Applies to all personnel with access to company systems, customer data, or financial processes, including agency and supplier staff who perform work for {{Company Name}}. Country-specific addenda form part of this policy.
Common mistakes to avoid
- Excluding contractors who can still log in to production or handle client funds.
- Writing a global statement without acknowledging local constraints.
Quick check
Can a new manager read your Purpose and Scope and understand exactly who is covered and why? If not, tighten it.
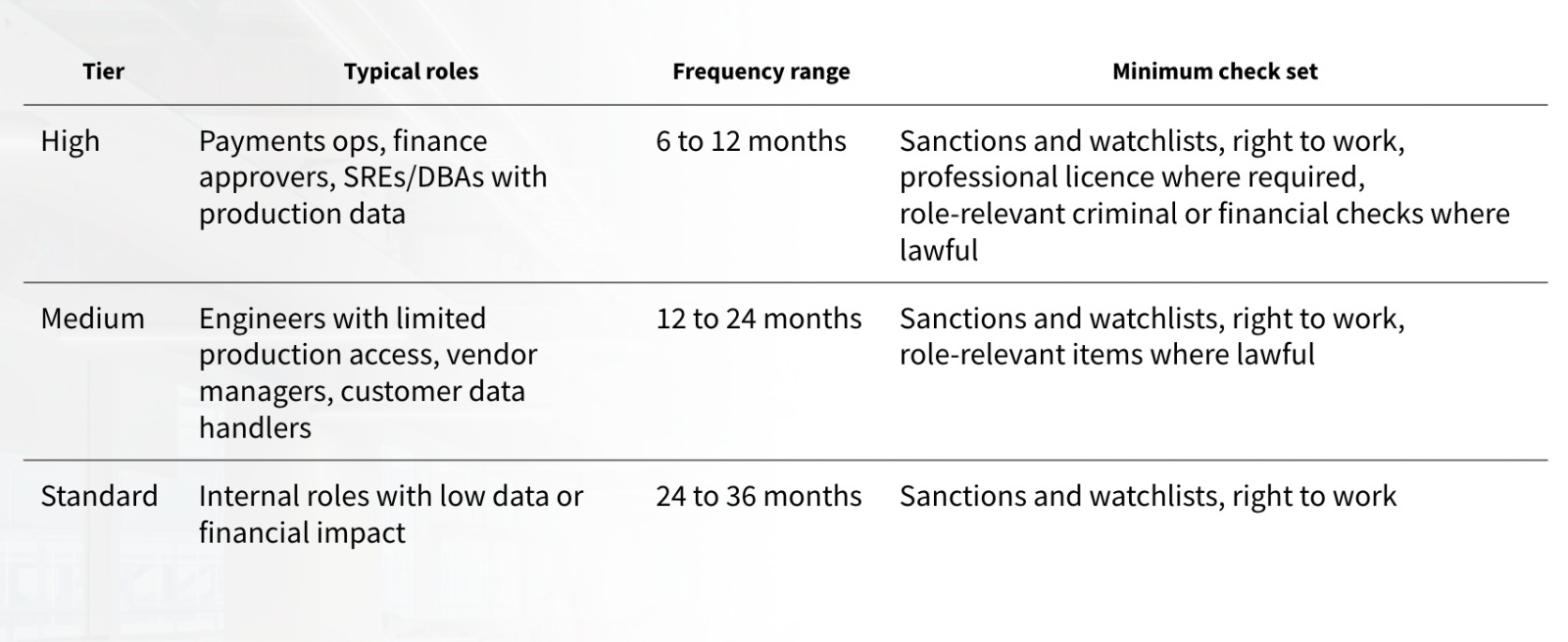
2) Cadence logic
Teach the concept
Frequency is the hardest part to defend. The right answer is risk-based. Use tiers and ranges, plus clear triggers for checks outside the schedule.
How to write it
- Group roles into three tiers by access and potential impact.
- Assign a range for each tier. Ranges are easier to defend than exact dates.
- Describe your “check set” per tier. Only include checks that are lawful and relevant.
- Define off-cycle triggers such as access changes and client requests.
Worked example
Trigger examples for off-cycle checks
- Access or role change that increases privileges
- Country relocation or change of employing entity
- Contractual request during client renewal or due diligence
- Incident that raises role risk
Teaching note
Publish your tier criteria in an appendix. If a role moves tier, the auditor should be able to see why.
3) Approvals and exceptions
Teach the concept
Auditors care about discipline. They want to see named owners, who can approve what, and how you control drift. Every exception needs a reason, an expiry and a compensating control.
How to write it
- Name the policy owners, such as Security and People.
- State who approves the tier model and the cadence ranges.
- Define who can grant an exception and for how long.
- Require compensating controls where you waive a check.
Example you can adapt
Ownership. The Chief Information Security Officer and Head of People jointly own this policy. Tier classifications and cadence ranges require their approval and are reviewed at least annually.
Exceptions. Any exception must name the risk owner, the reason, the expiry date and the compensating controls. Exceptions expire after 12 months unless re-approved.
Common mistakes to avoid
- Open-ended exceptions with no review date.
- Allowing line managers to grant exceptions without a risk owner.
Quick check
Pick a recent exception. Can you show who approved it, when it expires, and what control covers the risk until then?
4) Logging and evidence
Teach the concept
“If you cannot show it, it did not happen.” Build simple records that you can export in minutes.
How to write it
Create four artefacts and keep them consistent across teams.
- Approvals log
- Records for tier model, cadence ranges, and any exceptions.
- Fields: decision, approver, date, revocation date.
- Run log
- One row per person per cycle.
- Fields: name, role tier, checks performed, date completed, reviewer, outcome, next due.
- Exception register
- One row per exception.
- Fields: subject, reason, risk owner, compensating controls, expiry, status.
- Export index
- A cover sheet that lists where evidence lives and how to retrieve it.
Example run-log row
A. Sharma | High | Sanctions, right to work, licence re-check | 12 Apr 2025 | J. Tan | Pass | 12 Oct 2025
Teaching note
Redact personal data in exports by default. Keep the full record internally and share only what auditors need.
5) Renewals language and client commitments
Teach the concept
Account Managers will be asked for “proof that you rescreen.” Give them standard wording that maps to your policy and avoids over-promising.
How to write it
- Write one paragraph for due diligence questionnaires.
- Write one sentence for MSA clauses that you can accept.
- Link back to your evidence pack and scope.
Example you can adapt
Assurance for clients. {{Company Name}} operates a risk-based rescreening programme for personnel with access to customer data or financial processes. We can provide policy documents, cadence rationale and redacted evidence of recent cycles during renewals or audit sampling, subject to privacy and legal limits.
Common mistakes to avoid
- Promising specific checks in the MSA that may be unlawful in some countries.
- Agreeing to a fixed global cadence without referring to role risk.
Quick check
Can Sales copy your wording into a questionnaire today without legal rework? If not, simplify it.
6) Measuring effectiveness
Teach the concept
You must show that the control works and that you tune it over time. Choose a few measures you can keep up with.
How to write it
Pick three to five indicators and set a review rhythm.
Suggested KPIs
- Completion rate by tier and on-time percentage
- Exception rate by tier and average time to closure
- Time to produce a redacted evidence pack
- Audit and customer review outcomes related to screening
- Number of off-cycle triggers actioned after access changes
Example review note
Q4 review: High-tier on-time rate improved from 82 percent to 94 percent after IAM triggers were added. Exception rate dropped from 11 percent to 6 percent with expiry reminders. Evidence pack build time fell from five days to one day after standardising the export index.
Teaching note
Treat these as a feedback loop. If a KPI shows noise or delay, adjust cadence ranges, check sets or workflow.
Pulling it together
If you follow the steps above, your policy will read like a control that is designed and operated on purpose. It will show who is covered, why the cadence is proportionate, who approves exceptions, and how you can hand over clean evidence in days rather than weeks.
FAQs
FAQs
This depends on the industry and type of role you are recruiting for. To determine whether you need reference checks, identity checks, bankruptcy checks, civil background checks, credit checks for employment or any of the other background checks we offer, chat to our team of dedicated account managers.
Many industries have compliance-related employment check requirements. And even if your industry doesn’t, remember that your staff have access to assets and data that must be protected. When you employ a new staff member you need to be certain that they have the best interests of your business at heart. Carrying out comprehensive background checking helps mitigate risk and ensures a safer hiring decision.
Again, this depends on the type of checks you need. Simple identity checks can be carried out in as little as a few hours but a worldwide criminal background check for instance might take several weeks. A simple pre-employment check package takes around a week. Our account managers are specialists and can provide detailed information into which checks you need and how long they will take.
All Veremark checks are carried out online and digitally. This eliminates the need to collect, store and manage paper documents and information making the process faster, more efficient and ensures complete safety of candidate data and documents.
In a competitive marketplace, making the right hiring decisions is key to the success of your company. Employment background checks enables you to understand more about your candidates before making crucial decisions which can have either beneficial or catastrophic effects on your business.
Background checks not only provide useful insights into a candidate’s work history, skills and education, but they can also offer richer detail into someone’s personality and character traits. This gives you a huge advantage when considering who to hire. Background checking also ensures that candidates are legally allowed to carry out certain roles, failed criminal and credit checks could prevent them from working with vulnerable people or in a financial function.
Trusted by the world's best workplaces






APPROVED BY INDUSTRY EXPERTS
.png)
.png)




and Loved by reviewers
Transform your hiring process
Request a discovery session with one of our background screening experts today.







